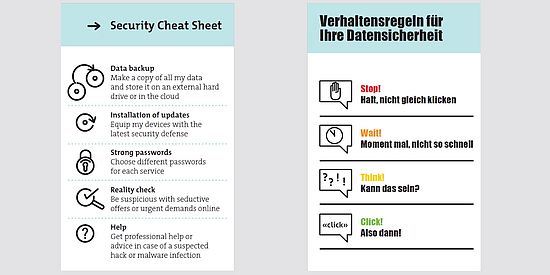
Most important rules of conduct for you
- Never send sensitive data such as passwords, PINs, TANs, etc. via e-mail.
- Check links to login pages very carefully.
Handling by IT Services
- If IT Services sends you an e-mail with a link to a login, this will be accompanied by a note to check links carefully.
- If IT Services receives a phishing e-mail from you, they will then initiate necessary measures to prevent further distribution of this e-mail, among other things.
- Due to the sometimes high volume of forwarded e-mails, you will not receive a reply to reported phishing e-mails.

Do I notice a malware on my computer?
Rather not! A good malware is of best use to its inventor if it is active on a computer for a longer period of time without being detected. Only then can the computer be misused for illegal purposes. Malware that massively impairs computer operation is now rather rare and is usually based on programming errors.
SHOW ANSWER
SHOW QUESTION
Quick Links
